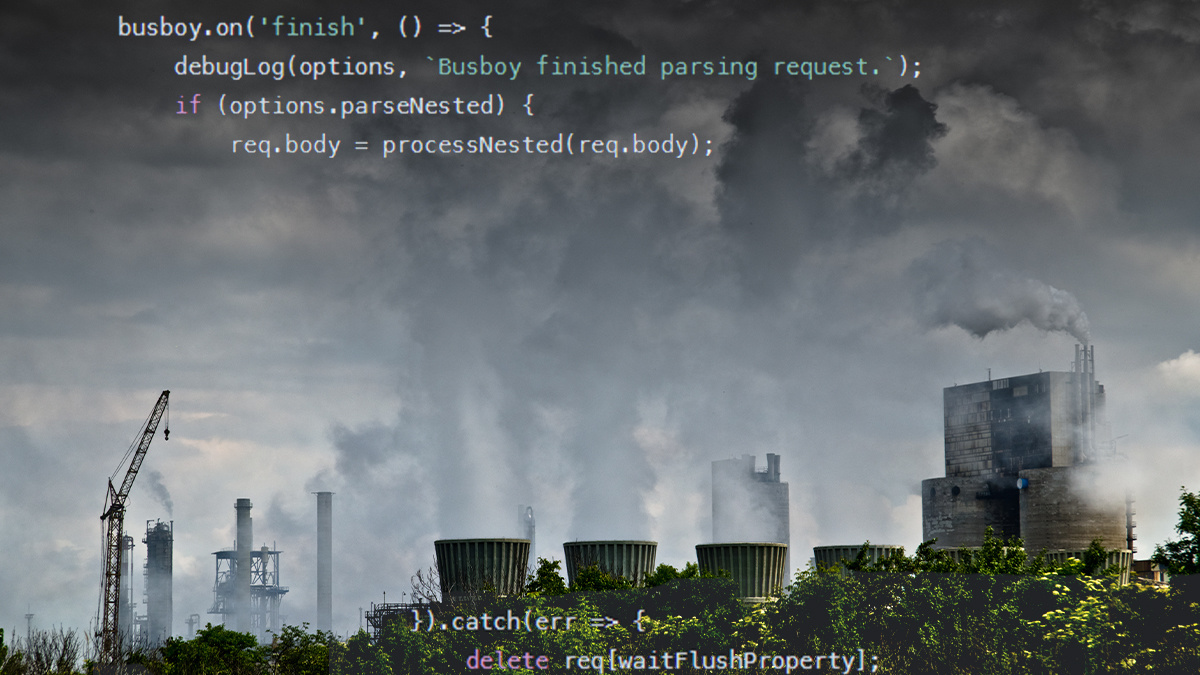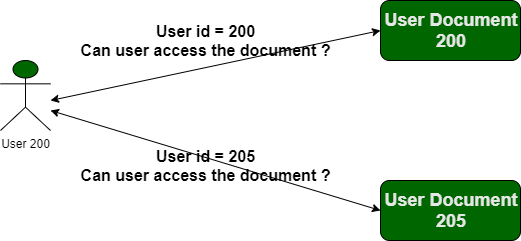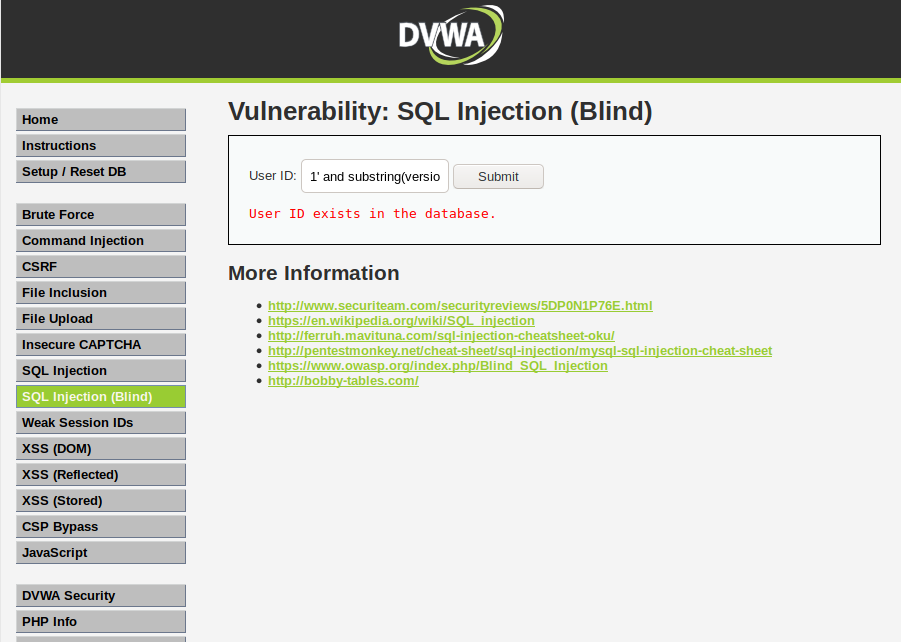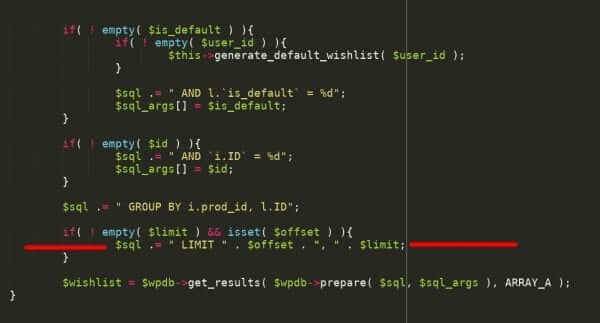
10 API Security Vulnerabilities You Need To Be Aware Of (Along with REST API Overview) | by Santosh Shinde | JavaScript in Plain English

Prototype pollution: The dangerous and underrated vulnerability impacting JavaScript applications | The Daily Swig

fuji 🌸 on Twitter: "jumping on the bandwagon to bring my ship dynamic. you'll never guess the ship https://t.co/BQ9XehoGDo" / Twitter

Remote code execution vulnerability exposed in popular JavaScript serialization package | The Daily Swig

New Research: Security Report Finds Ed Tech Vulnerability That Could Have Exposed Millions of Students to Hacks During Remote Learning – The 74

Prototype pollution: The dangerous and underrated vulnerability impacting JavaScript applications | The Daily Swig

Patrick Walton on Twitter: "This just in: Rust is useless because everyone who can write Rust already writes safe C code. I guess I've just been imagining every browser vulnerability of the

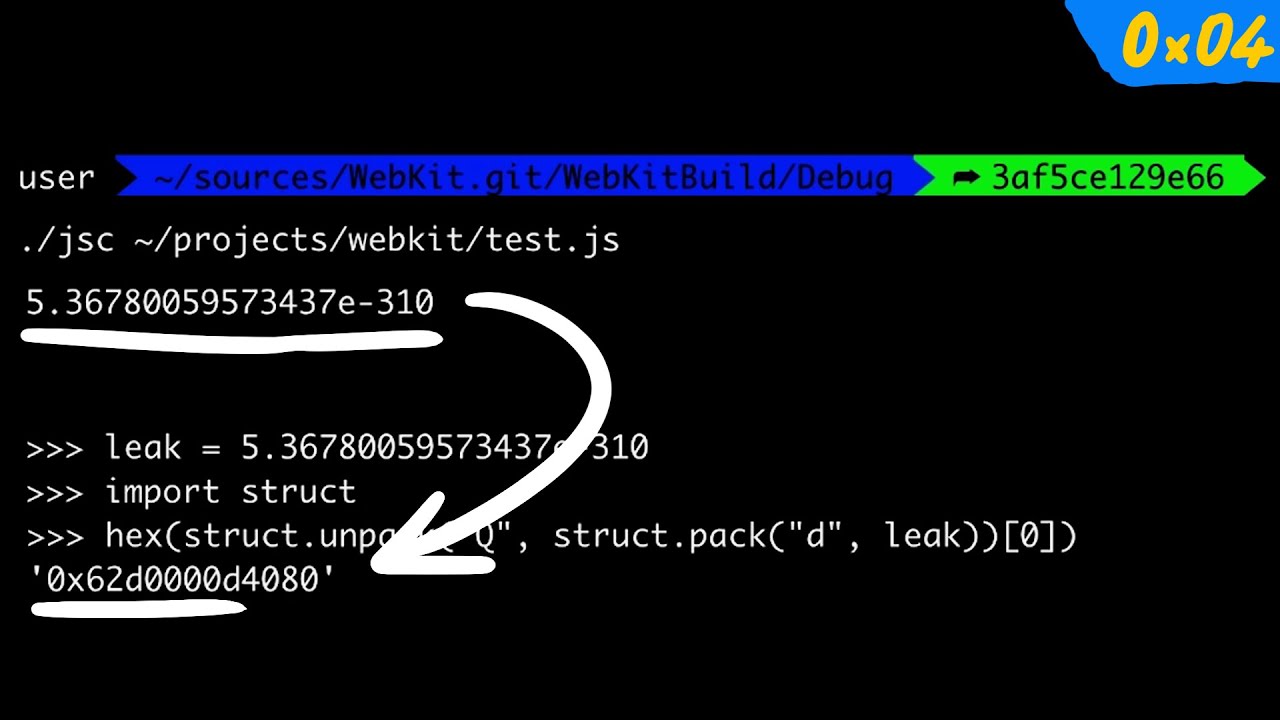
PS4 Webkit FontFace vulnerability: Sleirsgoevy publishes new Proof Of Concept, asks for tests with firmware 9.00 - Wololo.net